
ae03.alicdn.com/kf/Sd61952d2d8884688ad4b3d42a0a0e8

sparkle_H on X: #APT37 newly discovered samples Password.chm 6792d70638a294c823cbf6744cee5a13 압축파일 비밀번호.chm 99d2cfa7e63c6938e8849b6f96eb08f2 URL hxxp://yangak.com/data/cheditor4/pro/temp/7.html / X
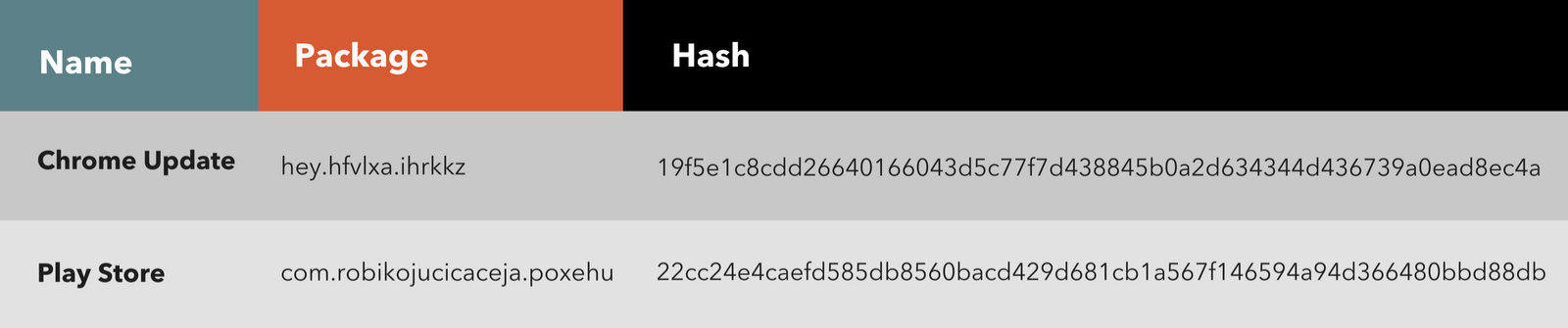
ERMAC 2.0 Evades MFA to Steal Banking Credentials of Over 400 Android Apps - Malware News - Malware Analysis, News and Indicators

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X
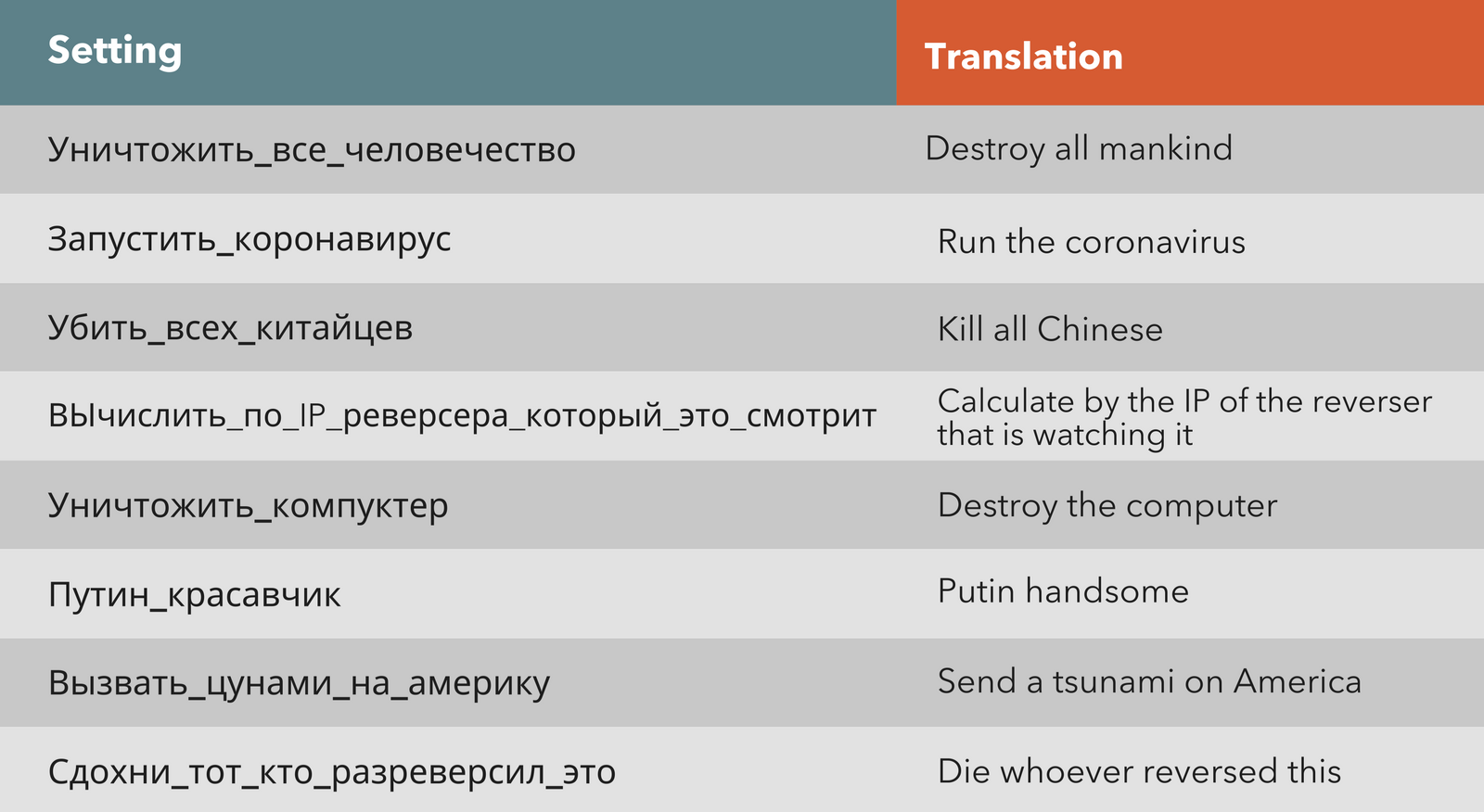
ERMAC 2.0 Evades MFA to Steal Banking Credentials of Over 400 Android Apps - Malware News - Malware Analysis, News and Indicators
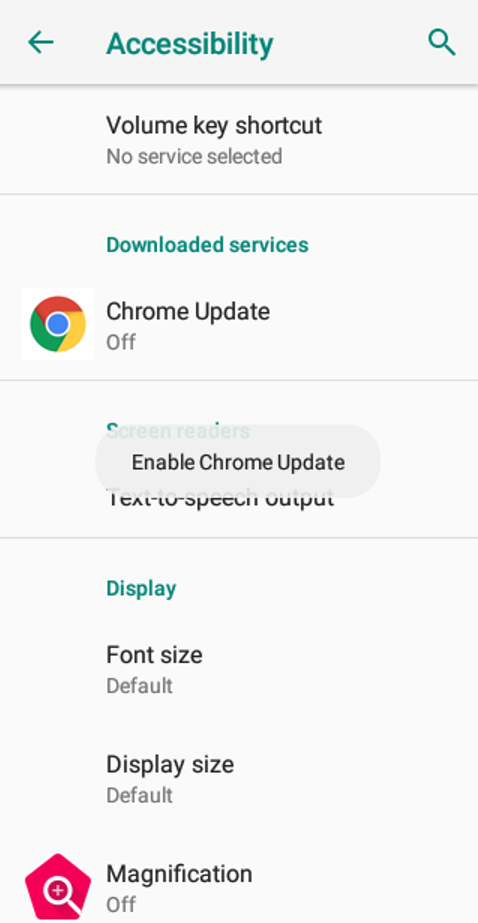
ERMAC 2.0 Evades MFA to Steal Banking Credentials of Over 400 Android Apps - Malware News - Malware Analysis, News and Indicators
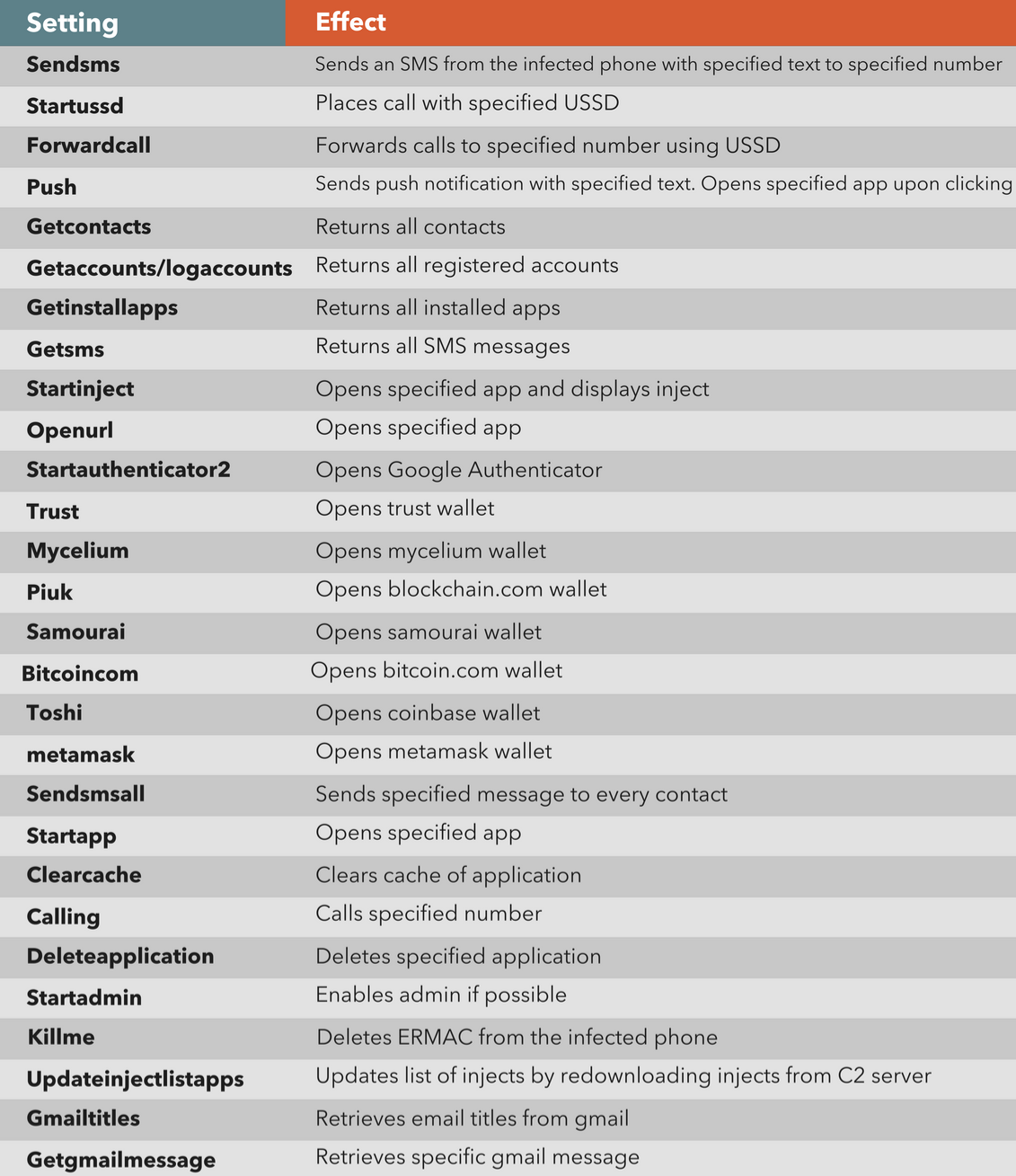
ERMAC 2.0 Evades MFA to Steal Banking Credentials of Over 400 Android Apps - Malware News - Malware Analysis, News and Indicators
Upload AnythingV5V3_v5PrtRE.safetensors · ducanvizla160/hihi at b808854
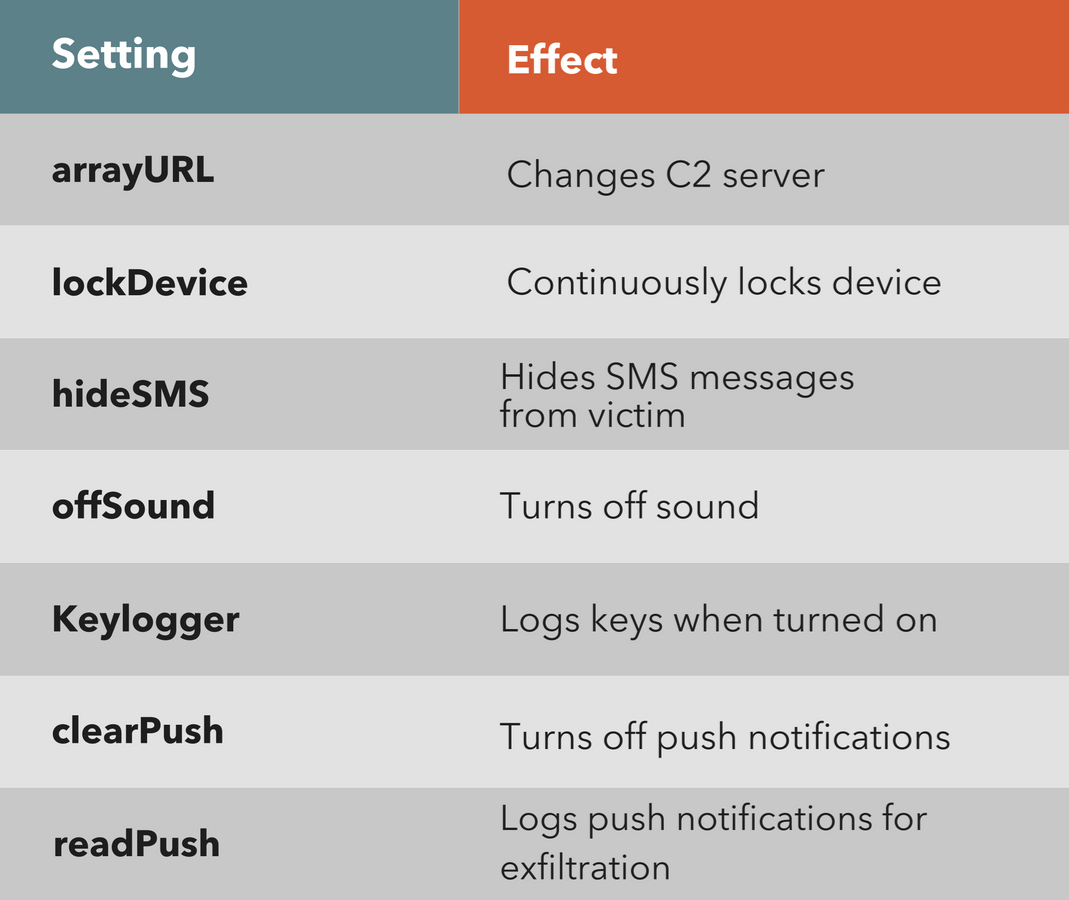
ERMAC 2.0 Evades MFA to Steal Banking Credentials of Over 400 Android Apps - Malware News - Malware Analysis, News and Indicators

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X

Nebula Revelation on X: 🚀 Exciting news! Our Certik Audit report is out now! 🖇️Certik Audit- 🚀NBL Contract-0x4B03afC91295ed778320c2824bAd5eb5A1d852DD ⏲️Plus, we've completed the token lock-up process to ensure added

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X

Abd Al HaDi/🚀MATR1XCoin (@Pa53796879) / X








